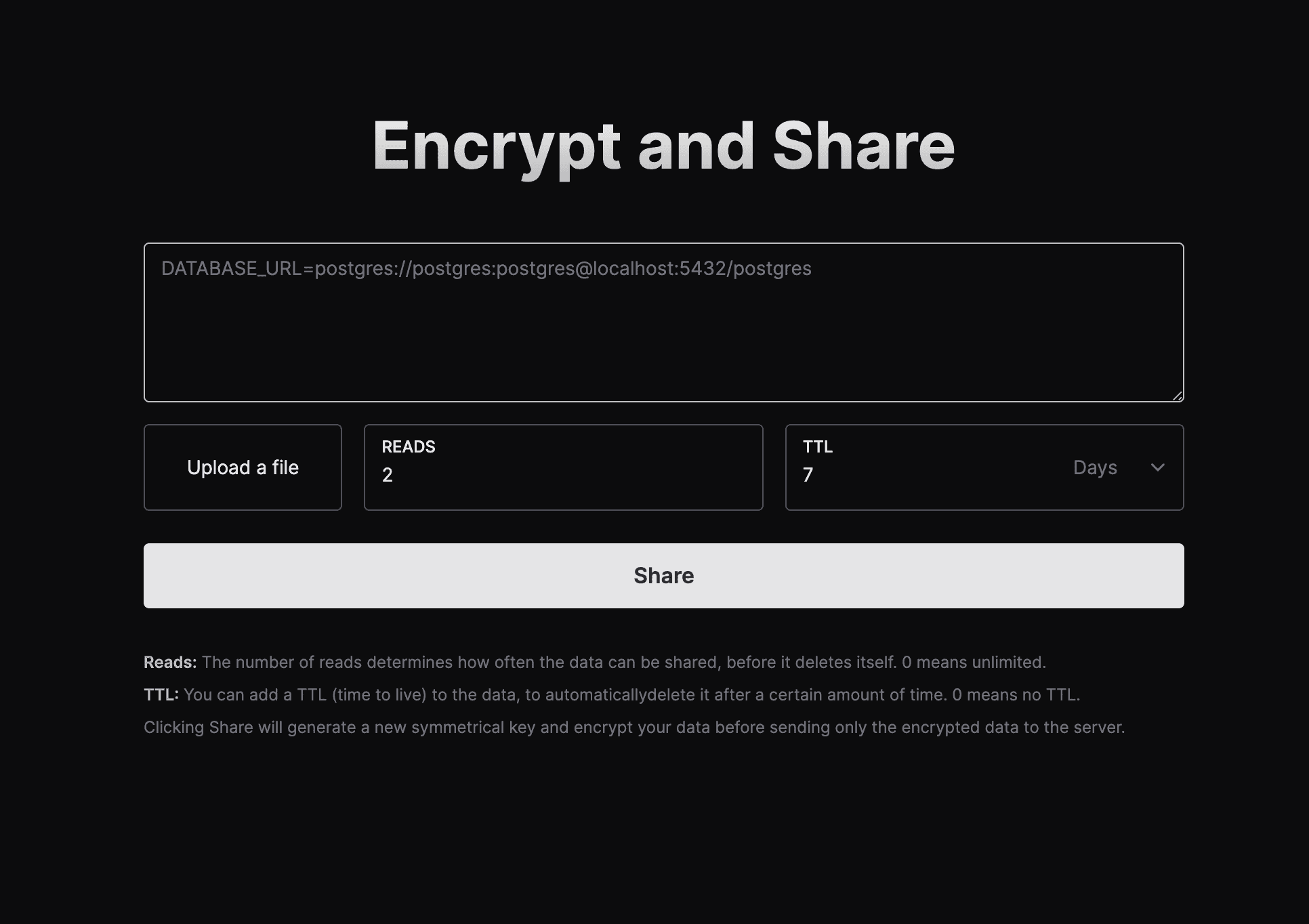
EnvShare is a simple tool to share environment variables securely. It uses AES-GCM to encrypt your data before sending it to the server. The encryption key never leaves your browser.
Features
- Shareable Links: Share your environment variables securely by sending a link
- End-to-End Encryption: AES-GCM encryption is used to encrypt your data before sending it to the server
- Limit number of reads: Limit the number of times a link can be read
- Auto Expire: Automatically expire links and delete data after a certain time
Built with
- Next.js
- tailwindcss
- Deployed on Vercel
- Data stored on Upstash
Deploy your own
Detailed instructions can be found here
All you need is a Redis database on Upstash and a Vercel account. Click the button below to clone and deploy:
Sponsors
Configuration
Environment Variables
ENABLE_VERCEL_ANALYTICS Any truthy value will enable Vercel Analytics. This is turned off by default
Contributing
This repository uses pnpm to manage dependencies. Install it using
npm install -g pnpm
Please run pnpm fmt before committing to format the code.
Docs
Docs in the README are temporary and will be moved to the website soon.
API
Store a secretPLEASE NEVER EVER UPLOAD UNENCRYPTED SECRETS.
This endpoint is only meant to store already encrypted secrets. The encrypted secrets are stored in plain text.
$ curl -XPOST -s https://envshare.dev/api/v1/secret -d "already-encrypted-secret"You can add optional headers to configure the ttl and number of reads.
$ curl -XPOST -s https://envshare.dev/api/v1/secret -d "already-encrypted-secret" -H "envshare-ttl: 3600" -H "envshare-reads: 10"- Omitting the
envshare-ttlheader will set a default of 30 days. Disable the ttl by setting it to 0. (envshare-ttl: 0) - Omitting the
envshare-readsheader will simply disable it and allow reading for an unlimited number of times.
This endpoint returns a JSON response with the secret id:
{ "data": { "id": "HdPbXgpvUvNk43oxSdK97u", "ttl": 86400, "reads": 2, "expiresAt": "2023-01-19T20:47:28.383Z", "url": "http://envshare.dev/api/v1/secret/HdPbXgpvUvNk43oxSdK97u" }}You need an id to retrieve a secret. The id is returned when you store a secret.
$ curl -s https://envshare.dev/api/v1/secret/HdPbXgpvUvNk43oxSdK97u{ "data": { "secret": "Hello", "remainingReads": 1 }}